An overview of GRC and SecOps tools
Think of the UCF as a Content Management System (CMS) in between various tool suites. Today’s...
Think of the UCF as a Content Management System (CMS) in between various tool suites. Today’s market is split between the following nine different types of tool vendors with the primaries being Governance Risk and Compliance (GRC) and Security Operations (SecOps):
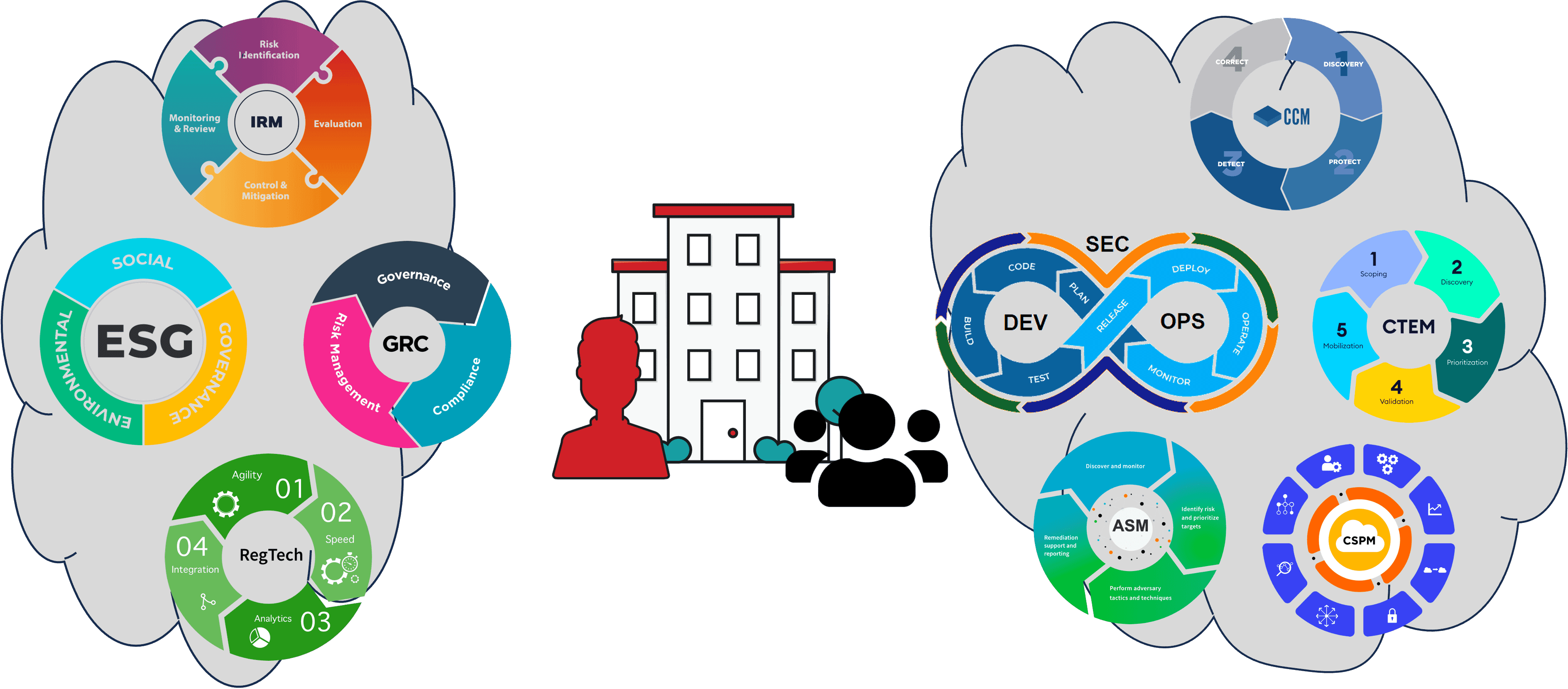
- GRC (Governance, Risk, and Compliance)
Purpose: GRC tools help organizations manage their governance, risk, and compliance with regulations.
Features: They often include modules for policy management, risk assessment, audit management, and compliance tracking.
Use Case: An organization might use a GRC tool to ensure they comply with applicable regulations and manage risks associated with their operations.
- ESG (Environmental, Social, and Governance)
Purpose: ESG tools help organizations measure, report, and improve their environmental, social, and governance performance.
Features: ESG tools provide metrics for sustainability performance, stakeholder engagement platforms, and reporting capabilities.
Use Cases: Companies utilize ESG tools to inform investment decisions, enhance reputation, and ensure sustainability in operations and supply chains.
- IRM (Integrated Risk Management)
Purpose: IRM tools offer a holistic approach to identify, assess, and manage risks across an organization.
Features: IRM tools integrate risk data from various sources, provide advanced analytics, and offer visualization tools for comprehensive risk oversight.
Use Cases: Businesses deploy IRM tools to gain a consolidated view of enterprise risks, drive strategic decision-making, and enhance resilience against threats.
- RegTech (Regulatory Technology)
Purpose: RegTech solutions help companies comply with regulations using technology. It’s especially prevalent in the financial sector.
Features: Automated compliance checks, reporting tools, and data analysis to ensure regulatory compliance.
Use Case: An organization might use RegTech solutions to ensure they adhere to financial regulations without manually checking every transaction.
- SecOps (Security Operations)
Purpose: SecOps tools facilitate the seamless integration of security and operations teams to enhance an organization’s security posture while ensuring operational efficiency.
Features: SecOps tools offer real-time threat detection, incident response capabilities, vulnerability management, and collaboration platforms for security and IT teams.
Use Cases: Organizations deploy SecOps tools to detect and respond to security threats promptly, automate security tasks, and foster collaboration between security and operations teams to reduce risks.
- CCM (Continuous Configuration Management)
Purpose: These tools ensure that systems and applications are securely configured, reducing the risk of vulnerabilities.
Features: Monitoring system configurations, detecting deviations from secure baselines, and automated remediation.
Use Case: An organization might use this tool to ensure that all their servers are configured securely and consistently, reducing the risk of a security breach due to misconfiguration.
- CTEM (Continuous Threat Exposure Management)
Purpose: This tool continuously monitors and assesses an organization’s exposure to cyber threats.
Features: Real-time monitoring, threat intelligence integration, and vulnerability assessment.
Use Case: An organization might use this tool to identify new vulnerabilities in their software or systems as soon as they are discovered.
- CSPM (Cloud Security Posture Management)
Purpose: CSPM tools ensure that cloud services and infrastructures are configured securely and compliant with best practices.
Features: Monitoring cloud configurations, detecting misconfigurations, and automated remediation suggestions.
Use Case: An organization using AWS or Azure might use CSPM to ensure their cloud setups are secure and not accidentally exposing sensitive data.
- ASM (Attack Surface Management)
Purpose: These tools identify and manage external digital exposures that an organization might have.
Features: Discovery of open ports, misconfigured services, exposed databases, and other potential entry points for attackers.
Use Case: Before launching a new product, an organization might use an attack surface management tool to ensure no unintended exposures.

